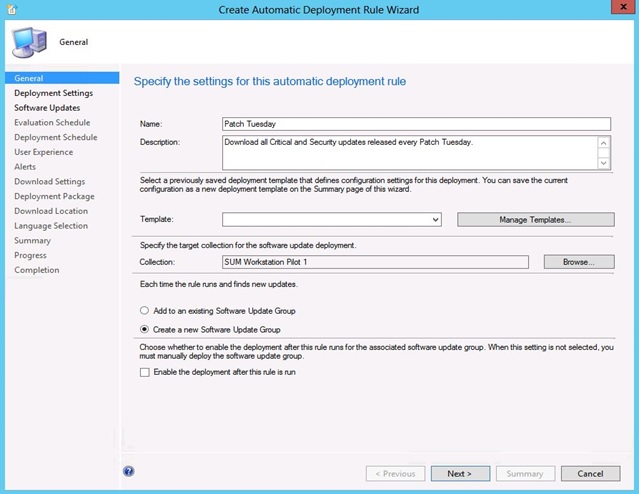
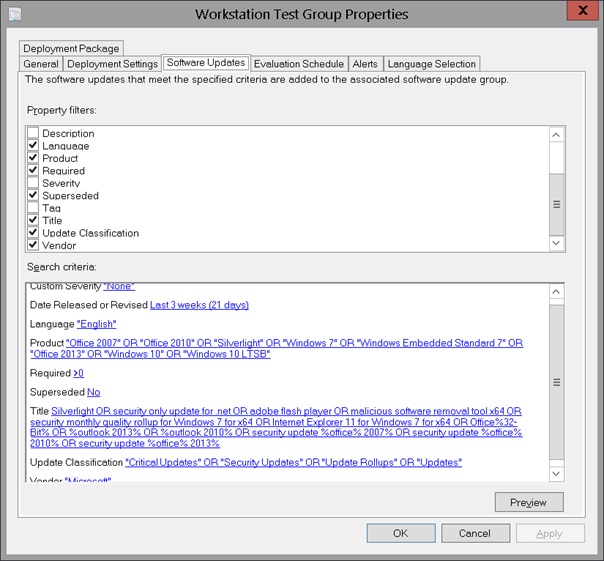
SCCM
includes an integrated WSUS server in it. You can set this Software Update
Point (SUP) to manage your environment windows updates. However, there most
likely will some problems along the way, below are the steps on how to
check the issue.
Client Side
Software update Components involved are:
1.Windows update agent (WUA)
2.Software update client agent (from
SCCM)
3.Windows management instrumentation
(WMI)
The Software Update process from the
ConfigMgr client
In the client side first thing we need
to check is the locationservices.log to make sure that the correct SUP point is
detected by the client, else make sure that the client is correctly reporting
to the SCCM server and that the software update is enabled. Make sure that the
server name and the port is specified correctly.
Locationservices.log
================
Calling back with the following WSUS
locations
LocationServices
4/29/2010 10:39:40 AM 2844 (0x0B1C)
WSUS
Path='https://SCCMCEN.SCS.IN:443', Server='SCCMCEN', Version='2'
LocationServices
4/29/2010 10:39:40 AM 2844
(0x0B1C)
Calling back with locations for WSUS
request
{10066528-1C1B-4A0C-958B-F29ACBEDBBDF}
LocationServices
4/29/2010 10:41:31 AM 2844 (0x0B1C)
Calling back with the following
distribution points
LocationServices
4/29/2010 11:27:23 AM 2552 (0x09F8)
Distribution
Point='\\SCCMCEN.SCS.IN\SMSPKGC$\CEN00003\4ea80bd5-c8ac-4f98-be8a-1c18f24a34e4',
Locality='LOCAL', DPType='SERVER', Version='6487',
Capabilities='<Capabilities SchemaVersion="1.0"><Property
Name="SSL" Version="1"/></Capabilities>',
Signature=''
LocationServices
4/29/2010 11:27:23 AM 2552 (0x09F8)
Now once the policy agent triggers the
scan cycle the windows update agent in the client will contact the WSUS server
which in our case is also the SUP point. Once the scan is successfully
completed this information is send as state message to the SCCM server. This
can be checked in windowsupadte.log or you can check WUAhandler.log under SCCM
client log.
WUAHandler.log
==============
Async searching of updates using WUAgent
started. WUAHandler
4/29/2010 10:42:20 AM 3488 (0x0DA0)
Async searching
completed.
WUAHandler 4/29/2010 11:24:21 AM 1496 (0x05D8)
Successfully completed
scan. WUAHandler 4/29/2010 11:24:25
AM 2752 (0x0AC0)
Its a WSUS Update Source type
({D4F72DDB-F6C4-4B05-835F-A8C23098857A}), adding
it.
WUAHandler 4/29/2010 11:25:24
AM 2752 (0x0AC0)
Existing WUA Managed server was already
set (https://SCCMCEN.SCS.IN:443), skipping Group Policy
registration.
WUAHandler 4/29/2010 11:25:25 AM 2752 (0x0AC0)
Added Update Source ({D4F72DDB-F6C4-4B05-835F-A8C23098857A})
of content type:
2
WUAHandler 4/29/2010 11:25:25
AM 2752 (0x0AC0)
Async searching of updates using WUAgent
started. WUAHandler
4/29/2010 11:25:25 AM 2752 (0x0AC0)
Async searching
completed. WUAHandler
4/29/2010 11:26:28 AM 2396 (0x095C)
Successfully completed
scan. WUAHandler 4/29/2010 11:26:32
AM 3756 (0x0EAC)
Now when the policy agent triggers the
software update deployment cycle the scan result is compared with the catalogue
and then it downloads only the required updates and install on schedule. You
can check the updatestore.log, updatedeploymemt.log for more details. You can
also check windowsupdate.log for more details.
Updatedeployment.log
==================
Service startup system
task UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
Software Updates
client configuration policy has not been received. UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
Software updates functionality will not
be enabled until the configuration policy has been received. If this issue
persists please check client/server policy
communication. UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
Software Updates feature is
disabled UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
Software Updates client configuration
policy has not been
received. UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
Software updates functionality will not
be enabled until the configuration policy has been received. If this issue
persists please check client/server policy
communication. UpdatesDeploymentAgent 4/28/2010
7:49:39 PM 3468 (0x0D8C)
………………….
…………………
Evaluation initiated for (1)
assignments. UpdatesDeploymentAgent 4/29/2010
10:39:20
AM 336
(0x0150)
Deadline received for
assignment ({3B1C5820-953D-4EFB-BDB7-3ABEE4C9788D}) UpdatesDeploymentAgent 4/29/2010
10:39:20 AM 3344
(0x0D10)
Enforcement trigger will be effective
when the current action completes UpdatesDeploymentAgent 4/29/2010
10:39:20
AM 3344
(0x0D10)
Message received: '<?xml
version='1.0' ?><SoftwareUpdatesMessage
MessageType='EvaluateAssignments'><UseCachedResults>True</UseCachedResults></SoftwareUpdatesMessage>' UpdatesDeploymentAgent 4/29/2010
10:39:30 AM 3940
(0x0F64)
Evaluation initiated for (0)
assignments. UpdatesDeploymentAgent 4/29/2010
11:01:55
AM 4064
(0x0FE0)
……………………………….
DetectJob completion
received for assignment ({3B1C5820-953D-4EFB-BDB7-3ABEE4C9788D}) UpdatesDeploymentAgent 4/29/2010
11:26:59 AM 3856
(0x0F10)
……………………..
Added update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_9fb3050e-26f2-4ccc-b9b0-b453ff58aaa9)
to the targeted list UpdatesDeploymentAgent 4/29/2010
11:26:59
AM 3856
(0x0F10)
Added update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_de919dec-2021-474a-8a7f-d632c2068146)
to the targeted
list UpdatesDeploymentAgent 4/29/2010
11:26:59
AM 3856
(0x0F10)
Added update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_d2e84b36-f0fd-4434-825d-a753a338b0bd)
to the targeted
list UpdatesDeploymentAgent 4/29/2010
11:26:59
AM 3856
(0x0F10)
……………………
Update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_de919dec-2021-474a-8a7f-d632c2068146)
Progress: Status = ciStateDownloading, PercentComplete
= 83, Result = 0x0 UpdatesDeploymentAgent 4/29/2010
11:27:36
AM 1068
(0x042C)
Progress received for assignment
({3B1C5820-953D-4EFB-BDB7-3ABEE4C9788D}) UpdatesDeploymentAgent 4/29/2010
11:27:38
AM 12
(0x000C)
DownloadJob completion
received for assignment ({3B1C5820-953D-4EFB-BDB7-3ABEE4C9788D}) UpdatesDeploymentAgent 4/29/2010
11:27:38
AM 12
(0x000C)
EnumerateUpdates for action
(UpdateActionInstall) - Total visible updates =
3 UpdatesDeploymentAgent 4/29/2010
11:27:38
AM 2960
(0x0B90)
Starting install for
assignment ({3B1C5820-953D-4EFB-BDB7-3ABEE4C9788D}) UpdatesDeploymentAgent 4/29/2010
11:27:38 AM 12
(0x000C)
………………….
Update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_de919dec-2021-474a-8a7f-d632c2068146)
Progress: Status = ciStateInstalling, PercentComplete = 100, DownloadSize = 0,
Result =
0x0 UpdatesDeploymentAgent 4/29/2010
11:31:26
AM 440
(0x01B8)
Update
(Site_D4F72DDB-F6C4-4B05-835F-A8C23098857A/SUM_de919dec-2021-474a-8a7f-d632c2068146)
Progress: Status = ciStatePendingSoftReboot, PercentComplete = 0, DownloadSize
= 0, Result =
0x0 UpdatesDeploymentAgent 4/29/2010
11:31:31
AM 3568
(0x0DF0)
CTargetedUpdatesManager - Job completion
received. UpdatesDeploymentAgent 4/29/2010
11:31:32 AM 496
(0x01F0)
Job Id =
{A807D023-9E41-4FE5-A528-6120C46C1134} UpdatesDeploymentAgent 4/29/2010
11:31:32 AM 496
(0x01F0)
No pending install
assignment UpdatesDeploymentAgent 4/29/2010
11:31:33 AM 440
(0x01B8)
EnumerateUpdates for
action (UpdateActionInstall) - Total visible updates =
3 UpdatesDeploymentAgent 4/29/2010
11:31:33
AM 2236
(0x08BC)
No installations in
pipeline, notify
reboot. UpdatesDeploymentAgent 4/29/2010
11:31:33
AM 440
(0x01B8)
Notify reboot with
deadline = Thursday, Apr 29, 2010. - 11:31:33, Ignore reboot Window =
False UpdatesDeploymentAgent 4/29/2010
11:31:33
AM 440
(0x01B8)
Update Deployment attempts to install
updates, Service Window Manager blocks the installation
(C:\Windows\CCM\Logs\UpdatesDeployment.log)
UpdatesDeployment.log
===================
Service Window Manager blocking the
installation
ServiceWindowManager.log
=======================
And when the window opens, the updates should install. Check the
UpdatesDeployment.log
The execution manager will have the following entries.
Execmgr.log
==========
Mandatory execution
requested for program Software Updates Program and advertisement {3D49D216-341B-4456-B52C-A0A480C06BEC} execmgr 4/29/2010
11:27:50
AM 2188
(0x088C)
Creating mandatory request for advert
{3D49D216-341B-4456-B52C-A0A480C06BEC}, program Software Updates Program,
package
{3D49D216-341B-4456-B52C-A0A480C06BEC} execmgr 4/29/2010
11:27:50
AM 2188
(0x088C)
CExecutionRequest::Overriding Service
Windows as per
policy. execmgr 4/29/2010
11:27:50 AM 2188
(0x088C)
Execution Manager timer has been
fired. execmgr 4/29/2010
11:27:50 AM 3256
(0x0CB8)
Executing
program in Admin context execmgr 4/29/2010
11:27:50 AM 2188
(0x088C)
Execution Request for package
{3D49D216-341B-4456-B52C-A0A480C06BEC} program Software Updates Program state change
from NotExist to
NotifyExecution execmgr 4/29/2010
11:27:50
AM 2188
(0x088C)
Executing program as an
update. execmgr 4/29/2010
11:27:51
AM 2188
(0x088C)
Executing Update
Program execmgr 4/29/2010
11:27:51 AM 2188
(0x088C)
Updates Installation started for the
passed command
line execmgr 4/29/2010
11:27:51
AM 2188
(0x088C)
Looking for MIF file to get program
status execmgr 4/29/2010
11:31:31
AM 440
(0x01B8)
Script
for Package:{3D49D216-341B-4456-B52C-A0A480C06BEC}, Program:
Software Updates Program succeeded with exit code
0 execmgr 4/29/2010 11:31:31
AM 440
(0x01B8)
Execution is complete
for program Software Updates Program. The exit code is 0, the execution status
is Success execmgr 4/29/2010
11:31:31
AM 440
(0x01B8)
The user has logged
off. execmgr 4/29/2010
11:38:13 AM 2788
(0x0AE4)
Once update is installed, then depending
on the reboot setting the system will be rebooted. This information is tracked
using RebootCoordinator.log
Also check the WindowsUpdate.log for update installation success
message
WindowsUpdate.log
=======================
And reboot if required (and scheduled)
RebootCoordinator.log
==================
Shutdown is already in
progress RebootCoordinator 4/29/2010
11:38:10
AM 3792
(0x0ED0)
Reboot
initiated RebootCoordinator 4/29/2010
11:38:10 AM 3792
(0x0ED0)
User logoff
notification
received RebootCoordinator 4/29/2010
11:38:13 AM 2788
(0x0AE4)
Shutdown is already in
progress RebootCoordinator 4/29/2010
11:38:17
AM 2788
(0x0AE4)
Reboot
initiated RebootCoordinator 4/29/2010
11:38:17 AM 2788
(0x0AE4)